

SecurEra’s consultants and subject-matter experts have proven records and expertise in implementing a robust process...

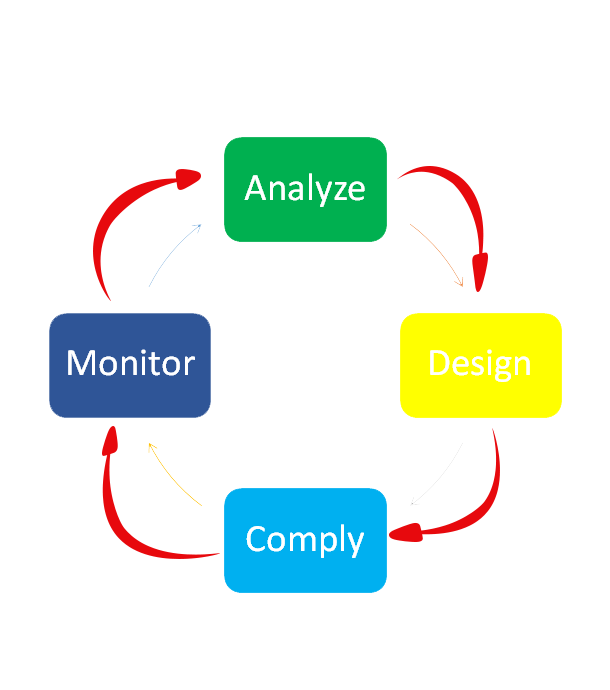
SecurEra’s consultants and subject-matter experts have proven records and expertise in implementing a robust process of understanding the customers’ requirements. This process is conducted through adequate analyzing and studying of the current information security status and designing the applicable controls and remediation plans to satisfy the business needs considering the acceptable risk appetite of the business. We then help customers to be compliant with related business or regional regulations and standards. Finally, we ensure the availability and effectiveness of existing monitoring mechanisms that make business vigilant, aware and resilient against any unpleasant events or incidents.
At SecurEra, we understand that risk assessment is the most important information security activity that an organization should perform. SecurEra Risk Management services are structured to be “Information Centric”, rather than technology centric, to help organizations understand the relevance of threat and vulnerability to their business. Our experienced security team is %100 focused on information security, and brings a wealth of experience to the table, as well as industry-recognized certifications and regulatory compliance expertise.
In today’s world, technology is changing very rapidly to meet end-users experience and business objectives. This leads to introduction of new vulnerabilities that can be exploited if not patched within time. SecurEra Vulnerability Assessment (VA) service helps our clients in identifying the vulnerabilities that may exist on all layers such as network, operating systems, databases and applications.
We normally start the process by invoking the following steps:
A penetration test is a proactive and authorized attempt to compromise information security and access sensitive data by taking advantage of vulnerabilities. SecurEra penetration testing services provide a comprehensive test of your internal and external security controls including your network & web applications. With our Penetration Testing service, our clients benefit from our extensive expertise in advanced penetration testing techniques, tools and methodologies as well as our excellent track record. SecurEra can cover the following areas:
A Security Network Architecture and Configurations Review enable you to know if your network architecture and the configuration of its components are compliant with the industry best practices and security recommendations.
The source code security review enables inspection of the application for accidental security vulnerabilities or deliberate application backdoors.
In order to effectively review a code baseline, our team understands the business purpose of the application and the most critical business impacts. This guides them in their search for serious vulnerabilities. The team also identifies the different threat agents, their motivation, and how they could potentially attack the application.
SecurEra team helps many organizations to have a clear and concise information security strategy that allows executives, management and employees to see where they are expected to go, focus their efforts in the right direction and know when they have accomplished their goals. Unfortunately, plenty of organizations lack an information security strategic plan, or at least one that is up to date. As a result, there’s a lack of focus and inconsistency in the actions taken across the enterprise, not to mention a greater likelihood of something bad happening.
We also help organizations build their own Security Governance. It’s very crucial to set responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately and verifying that the enterprise›s resources are used responsibly.
An information security management system (ISMS) is a set of policies and procedures for systematically managing an organization›s sensitive data. The goal of an ISMS is to minimize risk and ensure business continuity by pro-actively limiting the impact of a security breach.
At SecurEra , our team strives to make clients’ ISMS addresses employee behavior and processes as well as data and technology. It can be targeted towards a particular type of data, such as customer data, or it can be implemented in a comprehensive way that becomes part of the company›s culture.
Business Continuity Planning
A business continuity plan is a plan to continue operations if a place of business is affected by different levels of disaster which can be localized short term disasters, to days long building wide problems, to a permanent loss of a building. Such a plan typically explains how the business would recover its operations or move operations to another location after damage by events like natural disasters, theft, or flooding. For example, if a fire destroys an office building or data center, the people and business or data center operations would relocate to a recovery site.
SecurEra helps its clients in building a BCP and examine Business Impact Analysis (BIA) and Threat and Risk Analysis (TRA), Also ISO 22301 certification for organization.
SecurEra provides its clients with evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.
SecurEra utilizes both manual and automated intelligence sources and analysis capabilities.
An organization that accepts credit card payments, stores credit card data, processes credit card transactions must undergo PCI-DSS implementation and compliance. With several project experiences, our consultants are well qualified and experienced to deliver services in this area.
We have established strategic partnerships with leading Quality Security Assessors (QSA) companies as an enhancement of our service offerings. Our PCI-DSS services are made up of several phases, which can be customized as per the organization need as following:
“Boost Your Business with Industry Standard Compliance.” SecurEra is at the forefront of ISO 27001 certification consulting. SecurEra has already implemented major ISO 27001 projects with our clients. Our certified auditors and implementers can guide your company through the certification process and acceptance.
Our ISO 27001 Services can help you achieve certification includes:
SecurEra assists in designing and formulating the cycle of IT Governance, Risk and Compliance (GRC) initiatives for the organizations. Our consultants work directly with our clients and; in addition to provide an integrated GRC solutions; we have established strategic partnership with leading security, compliance and risk assessment organizations as an enhancement of our service offerings.
Organizations today face a variety of demands for external audits – including new laws and regulations, competitive pressure and technological change. SecurEra ‹s specialists rely on deep technical skills and industry knowledge to develop external audit functions with quality, efficiency and effectiveness. Our services include instituting risk-based IT audit strategies; performing IT audit projects; and providing ongoing expertise through co-sourcing arrangements.
Physical security is the protection of personnel, hardware, programs, networks, and data from physical circumstances and events that could cause serious losses or damage to an enterprise, agency, or institution. This includes protection from fire, natural disasters, burglary, theft, vandalism, and terrorism. Our consultants utilize leading best practices and standards when helping clients to build Physical Security requirements for Data Centers, systems, or sensitive sites. Human Safety is also becoming more important than in the past due to a direct interaction between personnel and systems.
The purpose of awareness programs is simply to focus attention on information security. Awareness programs are intended to allow individuals to recognize IT security concerns and respond accordingly. Awareness relies on reaching broad audience with attractive packaging techniques. At SecurEra , we develop customized awareness programs to our clients, which include:
SecurEra can help customers utilize world-class Security Awareness software, Learning Management Systems (LMS). It has high-quality educational content in various security topics such as: Phishing, Passwords, Wireless Security, Social Engineering, Portable Devices, Remote Access, Encryption, etc. It contains quizzes and other computer-based learning media.
IR is receiving a high demand nowadays due to many regional and technological circumstances. At SecurEra , our IR team provides immediate support and investigations to clients who need help in any of the following stages:
We provide our clients with appropriate Service Level Agreements that match their business needs and Risk Appetite when handling incidents. Our consultants provide support in finding and documenting evidence through proper forensic analysis and evidence collection process. For major incidents that require massive human-force analysis or technology, we utilize services of our international partners. Additionally, we help organizations that need to know their Response Readiness beforehand, in order for them to bridge any gaps existing in their process, staff, organization, tools, policies, skill sets, etc.